fwcloud & docker
fwcloud & docker
In the Docker section of the FWCloud installation section, we have already seen how to easily install FWCloud using Docker containers. Now we are going to describe in detail how to manage from FWCloud the security policy of a server in which Docker is being used, avoiding conflicts that may arise as a result of the IPTables rules that Docker automatically generates.
By default, Docker generates a set of IPTables rules appropriate to the containers it runs and the configurations defined for them. If we use FWCloud to manage the security policy of the server where we run our Docker containers, the rules automatically generated by Docker are removed when loading the FWCloud policy. And vice versa, Docker will generate IPTables rules that are not included in the security policy defined through our FWCloud console.
The best option to avoid these conflicts is to disable the automatic generation of IPTables rules by Docker and generate the appropriate security policy for our needs from FWCloud.
FWCloud & Docker compatibility consists of disabling IPTables in Docker and managing the security policy of our Docker server from FWCloud
Example
Next we will see a simple example of how to do this by running several containers on a Docker server, generating the necessary rules to allow the desired communications.
The first thing we need to do is disable the automatic generation of IPTables rules in our Docker installation. To do this we have to modify (or create if it does not exist) the following file:
/etc/docker/daemon.json
And verify that the iptables option is false or add it if it doesn’t already exist.
{ "iptables": false }
Next, we restart the Docker service to clean up any rules that may have been previously created.
sudo systemctl restart docker We make sure that there are no longer any rules generated by Docker using the following command, which should generate an output similar to the one we see below.
# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
If we see that there are still rules generated by Docker, it is best to restart the server to clean them up.
Next we are going to use two Docker containers, one based on the Ubuntu image in which we will execute a bash and the other with the Nginx image, exposing a TCP port to access it, in this way we will see how to allow access to it through the FWCloud policy.
docker run -ti ubuntu /bin/bash
docker run -d -p 8080:80 nginx
If we try to ping the ip 8.8.8.8 from the bash that we have launched in the container with the ubuntu image, we will see that it does not respond. This is because we have disabled Docker from automatically generating the IPTables rules that allow such communication. Therefore, we have to generate the necessary policy through FWCloud to allow this and any other communication flow that interests us.
Integration
Let’s see below how to generate the security policy in FWCloud to allow our Docker containers to access the Internet, as well as to enable access to the Nginx image container service.
To allow us to ping Internet IPs like 8.8.8.8 from our container with the Ubuntu image, we have to add two rules in the policy managed through our FWCloud console. The first one has to do a SNAT of the IP of our Docker container to the output IP of the computer on which it is running, so that we can access the Internet from such container.
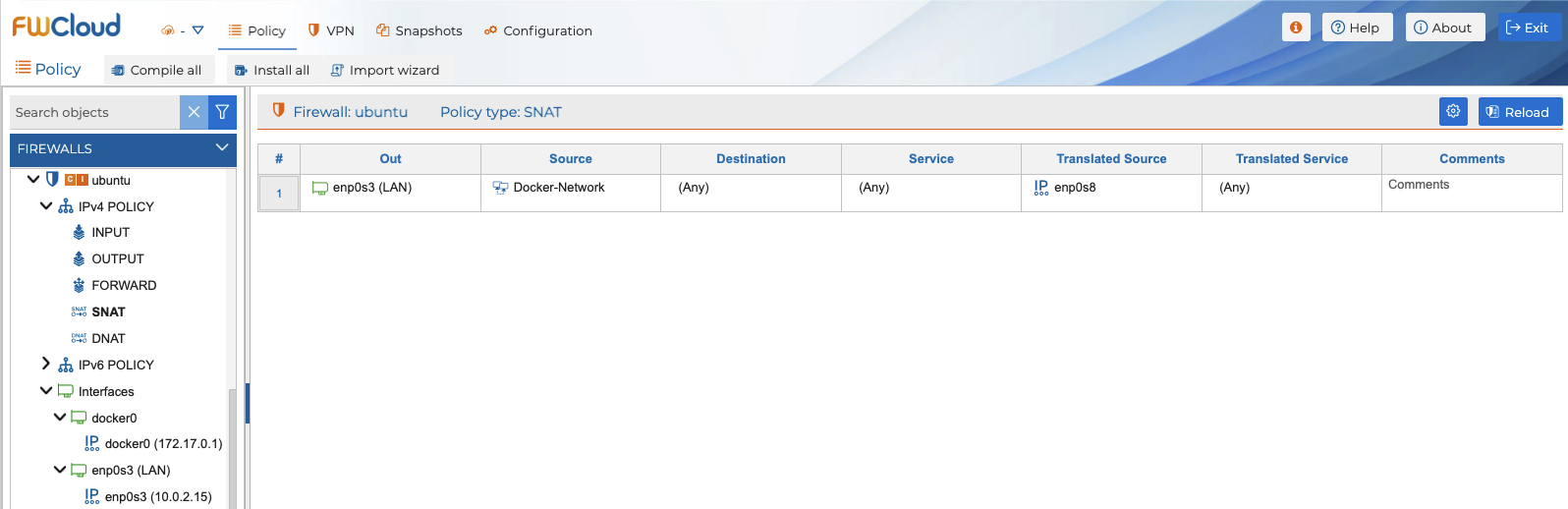
Now we need to allow traffic in the forward policy, entering through the virtual interface assigned to our container and leaving through the Internet access interface of the server on which we are running the container.
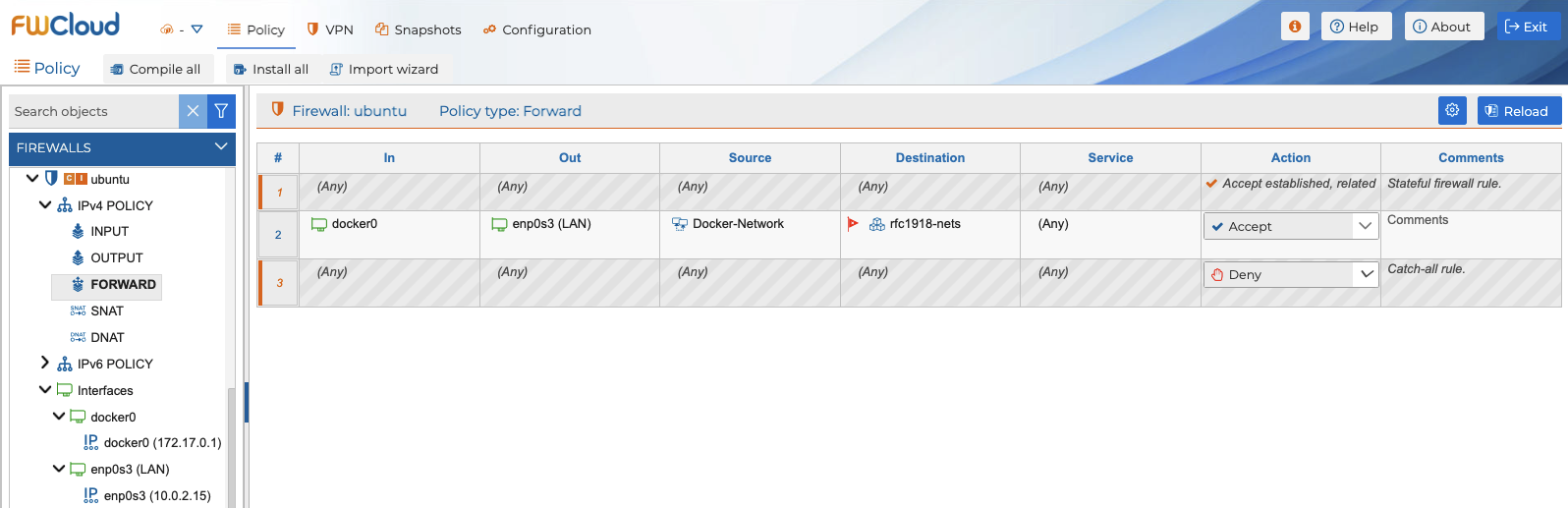
With these two rules we should already be able to ping the internet from the bash that we are running from our Docker container with the ubuntu image.
Next, to allow access to the other Docker container’s Nginx service, exposed via port 8080, all we need to do is allow that service in our firewall’s INPUT policy as shown in the following screenshot .
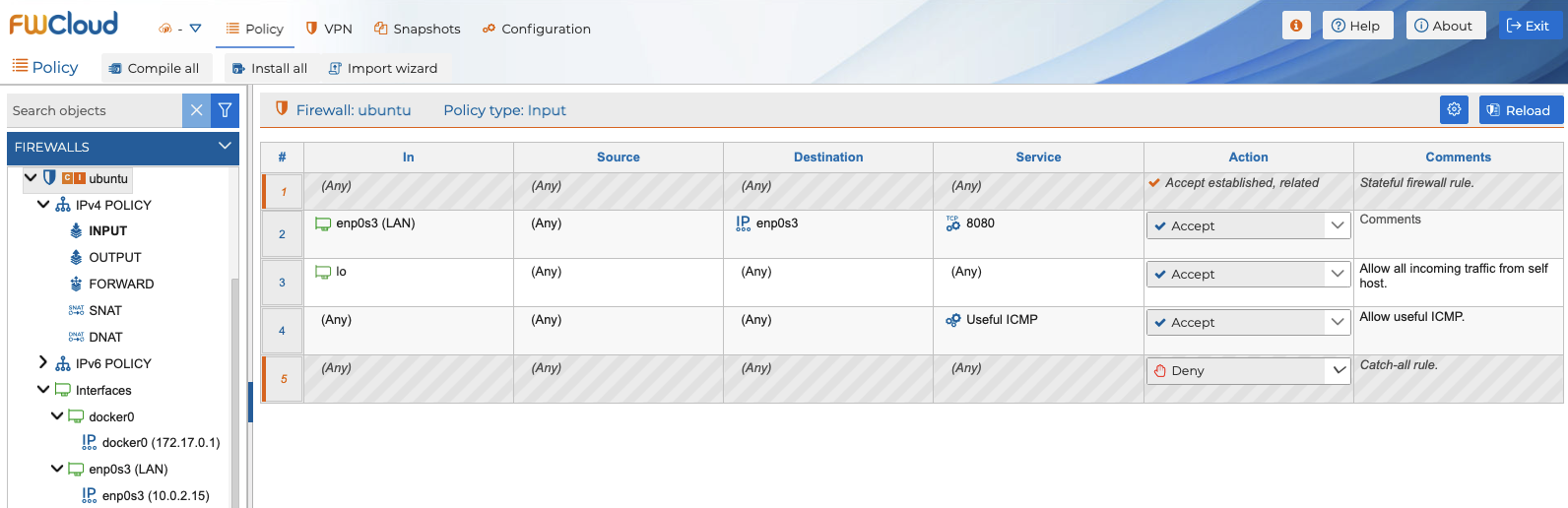
As can be seen from the example that we have just seen, it is very easy to define the necessary policy for the Docker containers executed on our server through FWCloud. Also, managing the policy from FWCloud instead of allowing Docker to generate it automatically gives us more control over the services and communications we want to allow.
FWCloud es un producto OpenSource con licencia GNU AGPL v3
